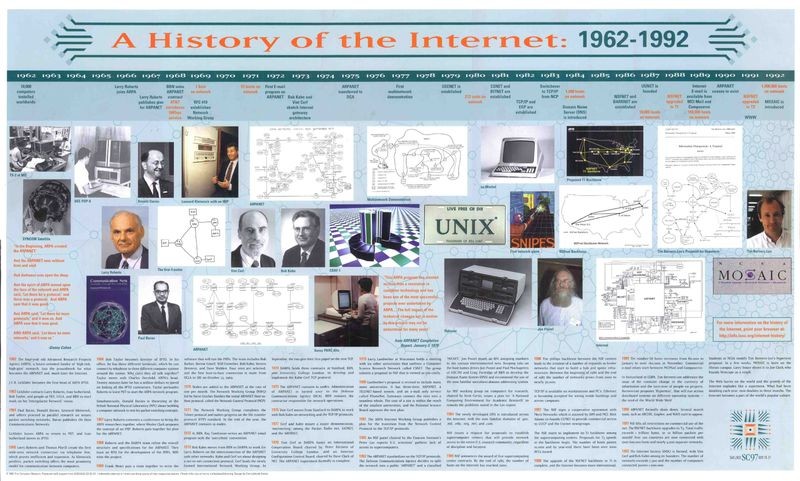
History of Computers and Computing, Internet

How will the entire world get on-line?
] a few VoIP providers provide an emergency service, however it is not universally out there. Older traditional telephones with no “extra features” could also be line-powered solely and function throughout an influence failure; VoIP can never do so with no backup power supply for the cellphone equipment and the Internet access gadgets. Pictures, paperwork, and other recordsdata are despatched as e mail attachments. The most prominent element of the Internet mannequin is the Internet Protocol (IP). IP enables internetworking and, in essence, establishes the Internet itself.
Nicholas G. Carr believes that Internet use has other effects on people, for instance bettering expertise of scan-reading and interfering with the deep pondering that results in true creativity. Lonely folks have a tendency to use the Internet as an outlet for his or her feelings and to share their stories with others, corresponding to within the “I am lonely will anybody communicate to me” thread. After English (27%), essentially the most requested languages on the World Wide Web are Chinese (25%), Spanish (8%), Japanese (5%), Portuguese and German (four% every), Arabic, French and Russian (three% every), and Korean (2%). By region, 42% of the world’s Internet users are based mostly in Asia, 24% in Europe, 14% in North America, 10% in Latin America and the Caribbean taken collectively, 6% in Africa, three% within the Middle East and 1% in Australia/Oceania. The Internet’s applied sciences have developed sufficient lately, particularly in the use of Unicode, that …